APIs are channels of communications, through which applications can “talk”. To create a connection between applications, REST APIs use HTTPS. HTTP requests pass through the API channel of communication and carry messages between applications.
Threat actors target REST APIs because they’re after the data stored in HTTP requests. Threat actors also use APIs to initiate attacks such as:
- Man in the Middle (MitM) — manipulates the communication contained within an API message.
- API injections (XSS and SQLi) — inject malicious code (malware or ransomware) into the API codebase or an API message.
- Distributed Denial of Service (DDoS) — repeated calls requesting API connections in fast succession, which is an attempt to overwhelm the server and create an outage. In this article, we’ll provide an overview of API concepts, and provide a table that summarizes the most essential OWASP recommendations for the security of REST APIs.
What is OWASP?
The Open Web Application Security Project (OWASP) is a non-profit organization committed to improving strengthening software security. They achieve this goal by providing unbiased educational resources, for free, on their website.
The OWASP website has a wealth of information, including community forums, documentation, videos, and free tools. Among these resources, you can find the OWASP top 10 vulnerabilities list, which has become a business-standard.
The OWASP top 10 was initially published in 2004 (and updated in 2017), born out of the need to identify the most critical vulnerabilities and prioritize remediation accordingly. While the top 10 list is an essential tool for software security, it’s not enough to keep networks protected.
An unfortunate misconception is that adhering to the OWASP top 10 list is all the security a piece of software requires. In reality, the software of today is built for connectivity and therefore is easily breached, which is why OWASP has created a cheat sheet for REST security.
What Is an Application Programming Interface (API)?
Connectivity between applications is achieved through an Application Programming Interface (API), which is a piece of software that opens and closes channels of communication. The API is composed of protocols, tools, and routines that enable data extraction and distribution.
Internet of Things (IoT) devices use APIs to communicate with each other, the network, the applications they control, and the applications that control them. A smart water heater switch, for example, won’t be able to remotely control the water heater without the use of an API. Web applications use web APIs to communicate with each other, the network, and IoT devices.
Connecting a social media account, for example, to a game application, requires the use of an API, another example are chrome extensions that in order to work with the browser, need to connect to the browsers API.
What is a REST API?
Representational State Transfer (REST) is an API implementation approach that uses the Hypertext Transfer Protocol (HTTP) to create connections. The REST API uses HTTP to gather data, transfer data and coordinates the execution of tasks between remote systems.
REST APIs mostly use JavaScript Object Notation (JSON) files to compress and transfer data from one web application to another. JSON files are small, and therefore easier to transfer, and they are also a standard web file, which means the recipient browsers would be able to read the file without any assistance from the API.
What Is REST Security?
To achieve secure communication, REST APIs use Hypertext Transfer Protocol Secure (HTTPS). A Transport Layer Security (TLS) protocol ensures that the connection is private (by encrypting the data), authenticated (through public-key cryptography), and reliable (through the use of a message authentication code).
REST APIs are stateless. To complete a connection, a REST API doesn’t need the client or the server. The HTTP request takes care of that by gathering and saving any requested information. This means that if threat actors gain access to the HTTP request, they gain access to the data.
REST security practices and solutions are entrusted with ensuring that any connection achieved through REST APIs is secured. REST security practices provide a guideline for developing and securing the APIS (as explained below), and the security solutions support these efforts.
What Is OWASP REST Security Cheat Sheet?
The OWASP REST security cheat sheet is a document that contains best practices for securing REST API. Each section addresses a component within the REST architecture and explains how it should be achieved securely.
The table below summarizes the key best practices from the OWASP REST security cheat sheet. For more information, please refer to the official documentation.
| REST API Component | Definition | Best Practices |
|---|---|---|
| HTTPS | A security protocol for communication between web applications | Protect authentication credentials in transit by providing only HTTPS endpoints, and add additional security through mutually authenticated client-side certificates |
| Access Control | A security method for regulating which users or systems access a device, software, or resource | Use an Identity Provider (IdP) for generating authentication tokens, and localize access control decisions to REST endpoints |
| JSON Web Tokens (JWT) | A standard format for security tokens that carry authentication claims | Always protect the integrity of the JWT with cryptographic signatures or MACs. Prefer signatures when possible, and always use standardized claims |
| API Keys | A unique sequence of Demand an API key for each request, use characters that authenticates API requests, and then answers or denies the call | Demand an API key for each request, use the 429 HTTP return code for too many requests, and withdraw API keys from clients that violate usage agreement |
| HTTP methods | A set of request methods (aka verbs) that implements the action that satisfies an HTTP request | Restrict HTTP methods through the use of method whitelists, apply the 405 return code for rejected methods, and authenticate the caller’s methods’ privileges. |
Implementing the OWASP REST Security Cheat Sheet
Securing your REST API doesn’t have to be difficult or even time-consuming. Sometimes, it’s only a matter of assessing your situation and then applying the appropriate fixes. In the section above, we reviewed key REST security best practices. Now, we’re going to provide you with a few pro tips to help you secure your APIs.
1. Applying the HTTPS-only standard
HTTPS is enabled through the use of Secure Socket Layer (SSL) certificates. The first step is to buy a certificate from your host provider. Next, you will need to install the certificate. This is done through the hosting panel, and it’s as simple as following the steps provided by the host.
Making your site HTTPS-only means going through your directories (such as client libraries, code examples, and sample applications), and replacing the calls from HTTP with HTTPS. You can do this manually, which takes time, or you can use a free search-and-replace tool.
2. Using an Identity Provider (IdP) for tokens
An IdP is a system that controls the process of creating and managing identity information and provides authentication services such as tokens generation. A token is a meaningless sequence of characters that replaces sensitive and financial information.
The IdP receives a request from the website to tokenize the information. Then, the system saves the information in a secure location and replaces it with a token. The IdP mediates between the user and the website, keeping the information safe in a third-party repository. You can find a list of IdPs here.
3. Cryptographic signatures for JWT
Digital signatures provide integrity, authentication, and non-repudiation, which makes them ideal for issuing tokens. You can delegate the task of generating tokens to an IdP (as explained above) or you can do this manually through the use of a verified OAuth 2.0 server.
You can build your own OAuth server, use the OAuth server sponsored by OKTA, and you can use open-source solution. Before committing to a path, assess your situation honestly, and ensure that you have the skills and resources to do this on your own.
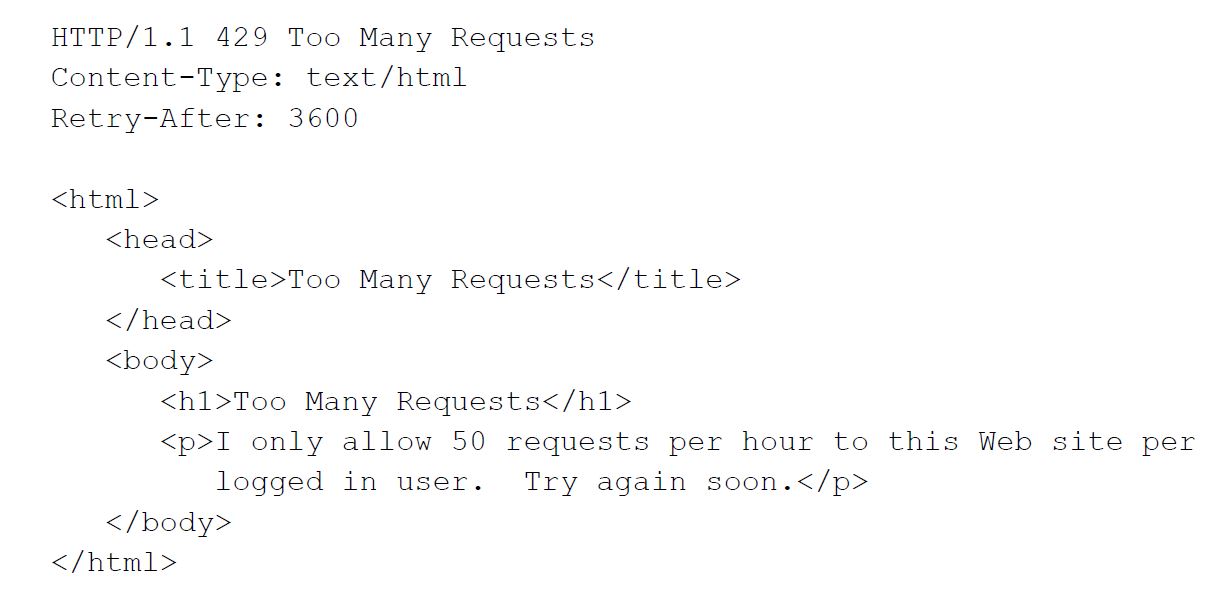
4. Add the 429 HTTP return code for too many requests
The purpose of the 429 return code is to prevent repeated API requests. It’s up to you to determine how many requests are too many in any given time, but this return code is a must. It provides you with a mechanism to provide DDoS attacks, which could cause a system outage.
Here’s a 429 code example from the RFC documentation:
Remember: never use a cache to store 429 status codes(!)
5. Use Cross-Origin Resource Sharing (CORS) for restricting HTTP methods
CORS is a technique that provides controls for sharing resources. That means you can use CORS to configure when access to HTTP methods should be granted or denied when it should be restricted, and what credentials and origins are authorized.
Be sure to research the subject, and configure your CORS properly. You can find a tutorial here, and here. If you don’t want to build from scratch, you can use this open-source CORS proxy. Be sure to test the code before running it, to make sure it’s as bug-free as possible.
It’s a Wrap!
In today’s hyper-connected world, there’s hardly any system that functions without an API. Networks, web applications, and IoT devices rely on their APIs for communication. An IoT device loses its meaning without an API. A web application can’t access data without an API, and endpoints can’t connect to networks without APIs.
REST APIs are entrusted with the communication between web applications. As most systems run web applications, insecure REST APIs could lead to breaches. A threat actor can cause a lot of damage by hacking only one REST API. To avoid a REST API breach, implement the OWASP REST security best practices and keep your APIs as secure as possible.
Author Bio
Gilad David Maayan is a technology writer who has worked with over 150 technology companies including SAP, Samsung NEXT, NetApp and Imperva, producing technical and thought leadership content that elucidates technical solutions for developers and IT leadership.